What is a VPN and how does it work?
A Virtual Private Network allows you to browse privately and anonymously by routing your device’s internet through the VPN network rather than your Internet Service Provider (ISP). As a result, when the data packets reach its destination, it will come from the VPN server rather than from your computer. Each device on the web has been assigned an IP Address. This is a unique address that gives the device its identity and helps in identifying the location from where the user is accessing the World Wide Web. These VPN services hide this IP Address and help you browse the internet in a safe and secure manner. In other words, think of a VPN as a tunnel or mediator that routes your data from its tunnel over to the final destination. And while doing so, it uses a protocol. There exist many different types of protocols, but some of the most used ones are the Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), Secure Socket Tunneling Protocol (SSTP), Internet Key Exchange version 2 (IKEv2) and OpenVPN. The first one, i.e PPTP is created by Microsoft and is the oldest one still in use. On the other hand, Open VPN is widely regarded as being the best VPN protocol around. Being open-source in nature, it is constantly upscaling the development chart.
Does Google Track you Browsing?
Yes, Google keeps a note on What you browse? How often you visit a particular website? Google actually stores cookies in the device hard drive, these cookies help in identifying the user and his behavior. It takes note of these cookies and shows the user target based ads. You can prevent Google from tracking you by using any secure search engine like DuckDuckGo.
What Information is sent to ISP?
As I mentioned earlier only URL’s and IP address is taken up by ISP for storing data. They do have any information on what you do on a website. Actually, whatever you do in HTTP is practically visible to everybody and is less secure but what you do in HTTPS is encrypted and more secure but ISP can still know the URL. Your passwords and other confidential information are secure from the service provider in HTTPS. Presently all search engines are using https// for online security.
What are the Benefits of a VPN?
There are a lot of perks associated with VPNs. For example, you could easily browse geo-restricted websites and access contents that are originally blocked for your region. Along the same lines, you get to access streaming services like Hulu, Disney, Netflix, etc that might not be available in your region. Likewise, you also get to browse the internet in a secure way, without being public. This goes a great length in providing anonymity from ISP tracking your activities and fighting off concerns relating to government monitoring your online activity, ISP collecting your data and browsing history, etc. Apart from that, you could also browse the public (open) wifi hotspots with greater security. Well, the list could go on and on. These are some of the major benefits associated with these VPNs services and as a result, are in huge demand nowadays.
What are the different types of VPN
Let us check out the different types of VPN services that Currently Exist
Corporate VPN
Corporate VPNs are generally used by employees working off-site. That is, they are remotely working and have to access important information from the office database. To make it a secure process they opt for the VPN route. Using a password, security token, or authenticator apps like Google Authenticator, Authy, etc they are able to securely login to their organization’s intranet and carry out the desired tasks.
Consumer VPN
The second type of VPN, this is used in large number by users across the world. In this type of VPN, you are able to connect to and access contents without any restriction or barrier. Acting as a tunnel, it helps you to connect to the destination by hiding your IP address and passing the connection through its server. This will make the ISP believe you are accessing the internet from the VPN’s region server rather than your own.
Standalone VPN
These are the VPN services provided by a single entity like Nord VPN, Tunnel Bear, Express VPN, etc. This allows you to easily set up a VPN on your PC and then try out its service without actually making the full commitment to it. For example, you could use these VPN services in a particular device like your laptop. For other devices connected to the network, they will work normally without any VPN. However, if you are satisfied with there services and wish to expand it to the network level, you could try the next VPN type mentioned below.
Router Level VPN
As the name suggests, it encapsulates the entire network under the VPN. As a result, any and every device connected to your router will go through this VPN service. Although it makes it pretty easy on your end but only go for this service on you are totally satisfied with that VPN, otherwise, you could continue to use the standalone VPNs.
Browser Extensions
Some VPNs also exists as a browser extension for Chrome, Firefox and other web browsers based on Chromium source code (like the new Microsoft Edge). On the other hand, there exist some dedicated VPN browsers like the Opera VPN as well. You could also try them out too.
How Secure are these VPNs
We have already mentioned that the VPN acts as a tunnel that helps in connecting you to your destination. For the uninitiated, the data that leaves your device are sent in packets. This is something that isn’t related to VPN but is how things work out in normal scenarios. Now as soon as these packets leave the source (i.e yojiur device), the VPN services wrap around an outer layer of protection to these packets which are encrypted through a process that we call as encapsulation. This outer package is responsible for keeping your data secure while it is transferred through the tunnel. And when the packets reach the destination, the outer packet is removed and decrypted. If for some reason, the connection is broken and your packets don’t reach the destination, then don’t worry, the intermediaries won’t be able to decrypt your data packets. Your data remains safe, secure, and in an encrypted state until it reaches its destination.
Any Performance Issues with these VPNs?
So in normal cases, the data packets leave the source and directly reach the destination. But while using a VPN service, each packet is first encapsulated and encrypted. Then when it reaches the destination, the outer packet is removed and then the decryption process takes place. This process will definitely take some time to complete. Likewise, the servers of this VPN are generally located geographically at far off places. You could choose a nearby server if a VPN offers, but it wouldn’t make much sense. For example, if you are an Indian user and want to access a blocked site, then you won’t be using a server of an Asian country but rather will choose a Europe or US server. This is because if a site is blocked in India, it might be blocked in neighboring Asian countries as well. But on choosing distant servers, we are also increasing the tunnel size through which these data packets have to pass. So in short, yes these VPN servers are somewhat slow since it has to pass through these processes, but still, you won’t notice a considerable decrease in speed. Furthermore, the positives attached to these VPNs definitely outweigh the negatives.
How to Connect to a VPN?
To connect to a public VPN, you could visit their respective sites. Some of the more popular VPN services include TunnelBear, Nord, ExpressVPN, etc. However, most of them are paid services. So please read all the features that they have in store, before proceeding ahead with the purchase. Also, before you start using the VPN service, you will have to create a profile. Here is how it could be done:
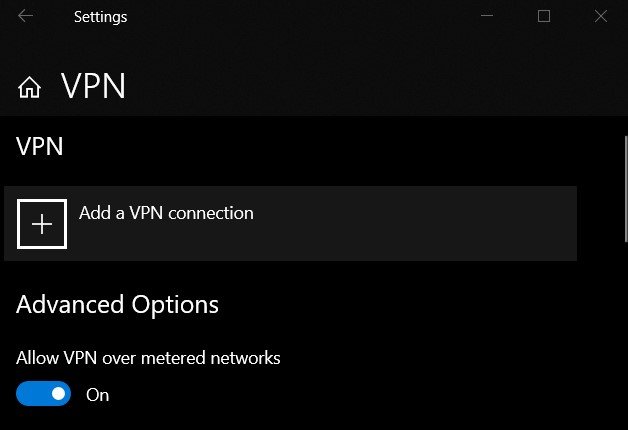
Click on the Start menu and type in a VPN. Open VPN Settings from the list.
Then click on Add a VPN connection situated at the top.
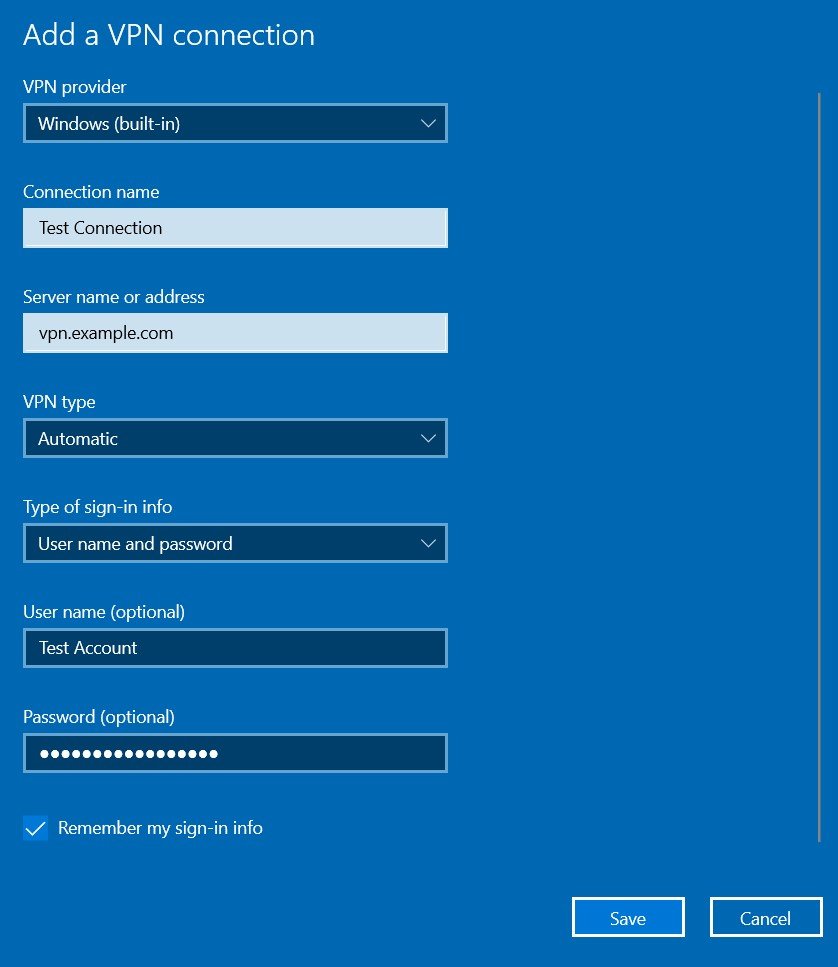
In the VPN provider box, select Windows (built-in).
Under the Connection name section, enter any name of your choice.
In the Server name or address box, enter the address of the VPN server.
Next, in the VPN type box, choose the VPN Protocol. Make sure to ask about this protocol from your organization or the place from where you would be using this VPN.
Now, select the Type of sign-in info. You could select a user name and password, a one-time password, a certificate, or a smart card if you’re connecting to a VPN for work.
Finally, enter the Username and Password if you want the connection to be more secure. It is optional though and you could skip it as well.
And if it is your own PC or laptop, you could tick the Remember my sign-in info as well. Once done, hit Save.
That’s it. You have successfully created a new VPN profile.
Conclusion
With that, we conclude this comprehensive guide on a VPN. We also discussed how to do a Virtual Private Network works, what protocol it uses and the steps to set it up. Likewise, we also did an in-depth coverage of the security aspect of these VPN services and their associated caveats. Top Best VPN Apps for iPhone With so many of its advantages, it is not surprising to see the usages of these VPN services upscaling the charts. What are your views on this? Are you currently using any VPN or have any plan to do so in the near future? Do let us know in the comments section below. If you’ve any thoughts on What is VPN and How it Works?, then feel free to drop in below comment box. Also, please subscribe to our DigitBin YouTube channel for videos tutorials. Cheers!